There are a several notable problems with many common drive retirement practices. Although not all of them are related to information security, many still result in excess cost. For example, companies that decide to re-purpose their hardware may choose to overwrite the data rather than erase it completely. The process itself is both time consuming, and a potential data security risk. For example, since re-allocated sectors on the drives are not covered by the overwrite process, this means that some old information will remain on disk.
Another option is to degauss and physically shred drives when the storage hardware is retired. Degaussing can yield mixed results, since different drives require unique optimal degauss strengths. This also often leads to readable data being left on the drive.
Thirdly, there is the option to hire professional disposal services to destroy the drive. However, the more people handling the data, the higher the data vulnerability. Total costs can also increase dramatically because of the need to publish internal reports and any auditing fees.
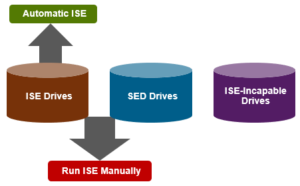
To address these issues, OneFS includes Instant Secure Erase (ISE) functionality. ISE enables the cryptographic erasure of non-SEDs drives in an Isilon cluster, providing customers with the ability to erase the contents of a drive after smartfail.
But first, some key terminology:
| Term | Definition |
| Cryptographic Erase | ‘SANITIZE’ command sets for SCSI/ATA drive is defined by the T10/T13 technical committees, respectively. |
| Instant Secure Erase | The industry term referring to the drive’s ‘cryptographic erase’ capability. |
| isi_drive_d | The OneFS drive daemon that manages the various drive states/activities, mapping devices to physical drive slots, and supporting firmware updates. |
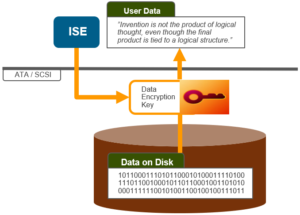
So OneFS ISE uses the ‘cryptographic erase’ command to erase proprietary user data on supported drives. ISE is enabled by default and automatically performed upon OneFS Smart-failing a supported drive.
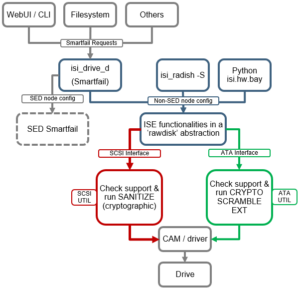
ISE can also be run manually against a specific drive. To do this, it sends standard commands to the drive, depending on its interface type. For example:
- SCSI: “SANITIZE (cryptographic)”
- ATA: “CRYPTO SCRAMBLE EXT”
If the drive firmware supports the appropriate above command, it swaps out the Data Encryption key to render data on the storage media unreadable.
In order to use ISE, the following requirements must be met:
- The cluster is running OneFS 8.2.1 or later.
- The node is not a SED-configuration (for automatic ISE action upon smartfail).
- User has privileges to run related CLI commands (for manually performed ISE).
- For example, the privilege to run ‘isi_radish’.
- Cluster contains currently supported drives:
- SCSI / ATA interface.
- Supports “cryptographic erase” command.
- The target drive is present.
ISE can be invoked by the following methods:
- Via the isi_drive_d daemon during a drive Smartfail.
- If the node is non-SED configuration.
- Configurable through ‘drive config’.
- Manually, by running the ‘isi_radish’ command.
- Programmatically, by executing the python ‘isi.hw.bay’ module.
As mentioned previously, ISE is enabled by default. If this is not desired, it can be easily disabled from the OneFS CLI with the following syntax:
# isi devices drive config modify --instant-secure-erase no
The following CLI command can also be used to manually run ISE:
# isi_radish -S <bay/dev>
ISE provides fairly comprehensive logging, and the results differ slightly depending on whether it is run manually or automatically during a smartfail. Additionally, the ‘isi device drive list’ CLI command output will display the drive state. For example:
| State | Context |
| SMARTFAIL | During ISE action |
| REPLACE | After ISE finish |
Note that an ISE failure or error will not block the normal smartfail process.
For a manual ISE run against a specific drive, the results are both displayed on the OneFS CLI console and written to /var/log/messages.
The ISE logfile warning messages include:
| Action | Log Entry |
| Running ISE | “Attempting to erase smartfailed drive in bay N …”,
“Drive in bay N is securely erased” (isi_drive_history.log) “is securely erased: bay:N unit:N dev:daN Lnum:N seq:N model:X …” |
| ISE not supported | “Drive in bay N is not securely erased, because it doesn’t support crypto sanitize.” |
| ISE disabled in drive config | “Smartfailed drive in bay N is not securely erased. instant-secure-erase disabled in drive_d config.” |
| ISE error | “Drive in bay N is not securely erased, attempt failed.”
“Drive in bay N is not securely erased, can’t determine if it supports crypto sanitize.” (isi_drive_history.log) “failed to be securely erased: bay:N unit:N dev:daN Lnum:N seq:N model:X …” |
When troubleshooting ISE, a good first move is using the CLI ‘grep’ utility to search for the keyword ‘erase’ in log files.
| Symptom | Detail |
| ISE was successful but took too long to run | • It depends on drive model, but usually < 1minute
• It may block other process from accessing the drive.
|
| ISE reports error | • Usually it’s due to CAM got error sending sanitize commands
• Looking at console & /var/log/messages & dmesg for errors during ISE activity timeframe – Did CAM report error? – Did the device driver / expander report error? – Did the drive/device drop during sanitize activity?
|