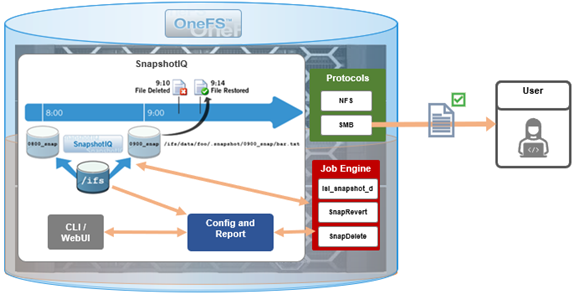
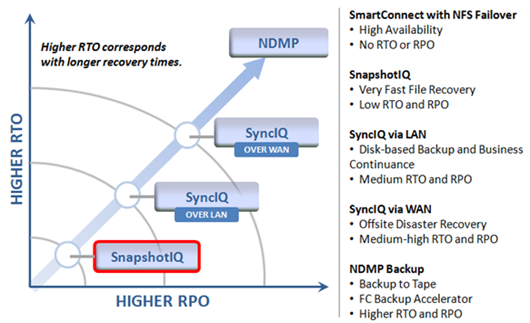
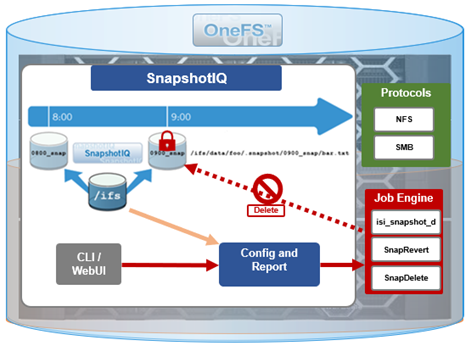
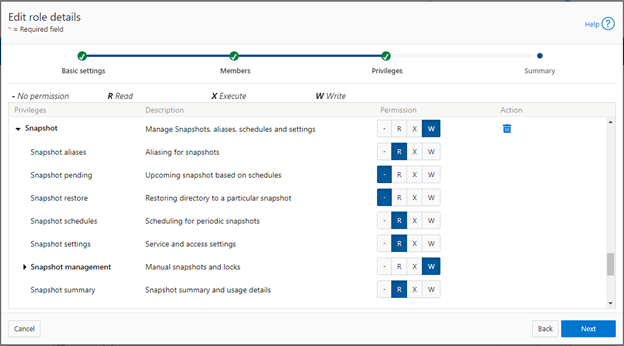
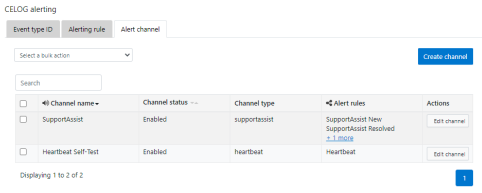
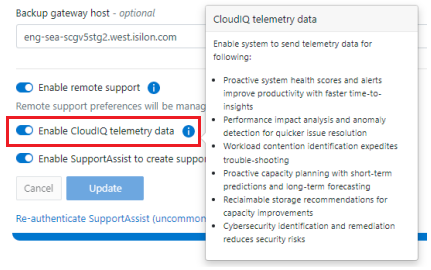
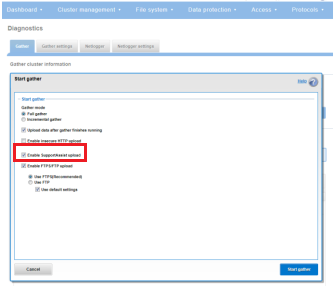
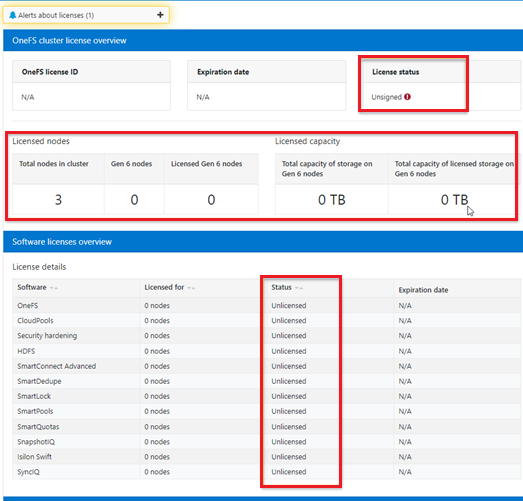
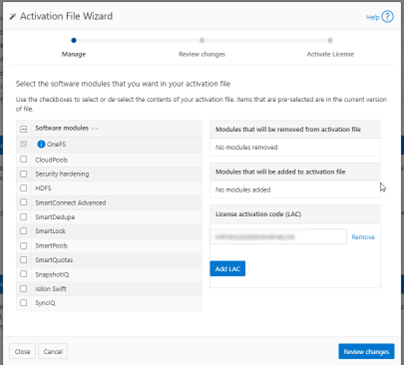
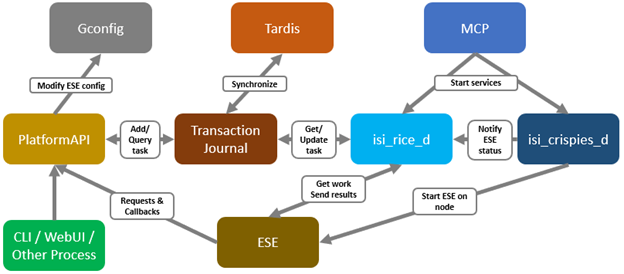
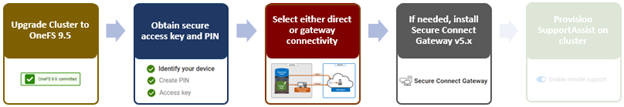
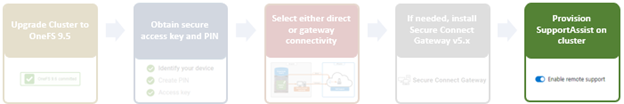
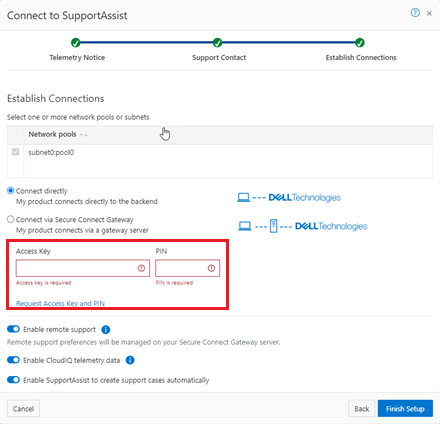
Among the array of security features introduced in OneFS 9.5 is a new host-based firewall. This firewall allows cluster administrators to configure policies and rules on a PowerScale cluster in order to meet the network and application management needs and security mandates of an organization.
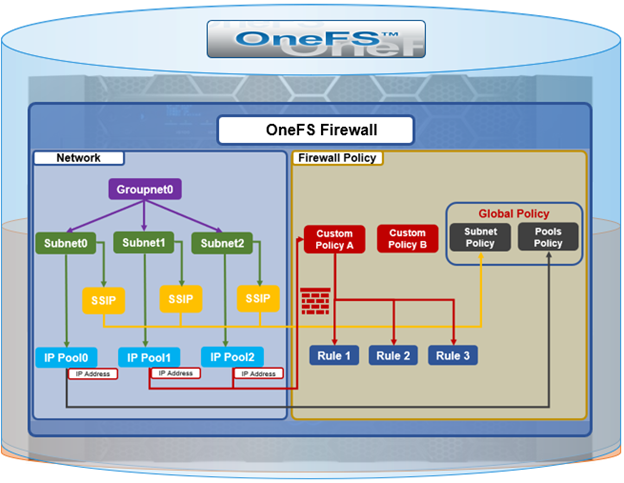
The OneFS firewall protects the cluster’s external, or front-end, network and operates as a packet filter for inbound traffic. It is available upon installation or upgrade to OneFS 9.5, but is disabled by default in both cases. However, the OneFS STIG hardening profile automatically enables the firewall and the default policies, in addition to manual activation.
The firewall generally manages IP packet filtering in accordance with the OneFS Security Configuration Guide, especially in regards to the network port usage. Packet control is governed by firewall policies, which are comprised of one or more individual rules.
| Item | Description | Match | Action |
| Firewall Policy | Each policy is a set of firewall rules. | Rules are matched by index in ascending order | Each policy has a default action. |
| Firewall Rule | Each rule specifies what kinds of network packets should be matched by Firewall engine and what action should be taken upon them. | Matching criteria includes protocol, source ports, destination ports, source network address) | Options are ‘allow’, ‘deny’ or ‘reject’. |
A security best practice is to enable the OneFS firewall using the default policies, with any adjustments as required. The recommended configuration process is as follows:
| Step | Details |
| 1. Access | Ensure that the cluster uses a default SSH or HTTP port before enabling. The default firewall policies block all nondefault ports until you change the policies. |
| 2. Enable | Enable the OneFS firewall. |
| 3. Compare | Compare your cluster network port configurations against the default ports listed in Network port usage. |
| 4. Configure | Edit the default firewall policies to accommodate any non-standard ports in use in the cluster. NOTE: The firewall policies do not automatically update when port configurations are changed. |
| 5. Constrain | Limit access to the OneFS Web UI to specific administrator terminals |
Under the hood, the OneFS firewall is built upon the ubiquitous ‘ipfirewall’, or ‘ipfw’, which is FreeBSD’s native stateful firewall, packet filter and traffic accounting facility.
Firewall configuration and management is via the CLI, or platform API, or WebUI and OneFS 9.5 introduces a new Firewall Configuration page to support this. Note that the firewall is only available once a cluster is already running OneFS 9.5 and the feature has been manually enabled, activating the isi_firewall_d service. The firewall’s configuration is split between gconfig, which handles the settings and policies, and the ipfw table, which stores the rules themselves.
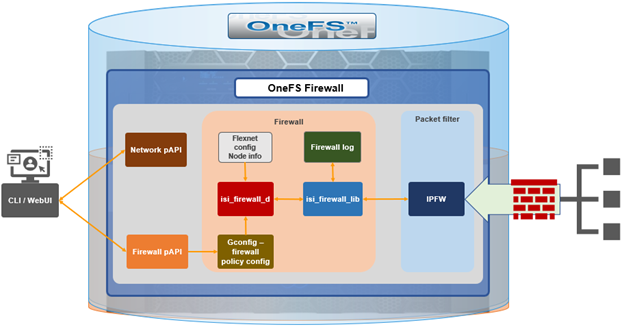
The firewall gracefully handles any SmartConnect dynamic IP movement between nodes since firewall policies are applied per network pool. Additionally, being network pool based allows the firewall to support OneFS access zones and shared/multitenancy models.
The individual firewall rules, which are essentially simplified wrappers around ipfw rules, work by matching packets via the 5-tuples that uniquely identify an IPv4 UDP or TCP session:
- Source IP address
- Source port
- Destination IP address
- Destination port
- Transport protocol
The rules are then organized within a firewall policy, which can be applied to one or more network pools.
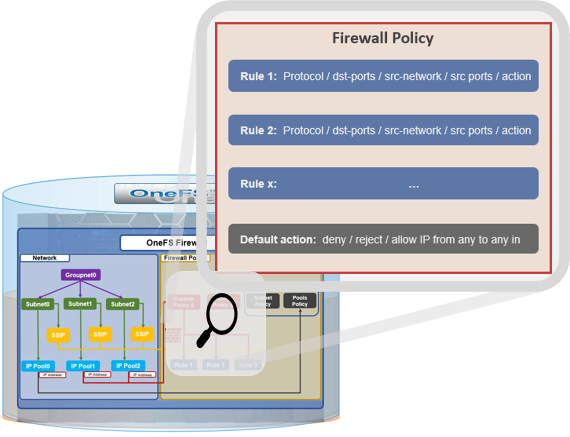
Note that each pool can only have a single firewall policy applied to it. If there is no custom firewall policy configured for a network pool, it automatically uses the global default firewall policy.
When enabled, the OneFS firewall function is cluster wide, and all inbound packets from external interfaces will go through either the custom policy or default global policy before reaching the protocol handling pathways. Packets passed to the firewall are compared against each of the rules in the policy, in rule-number order. Multiple rules with the same number are permitted, in which case they are processed in order of insertion. When a match is found, the action corresponding to that matching rule is performed. A packet is checked against the active ruleset in multiple places in the protocol stack, and the basic flow is as follows:
- Get the logical interface for incoming packets
- Find all network pools assigned to this interface
- Compare these network pools one by one with destination IP address to find the matching pool (either custom firewall policy, or default global policy).
- Compare each rule with service (protocol & destination ports) & source IP address in this pool from in order of lowest index value. If matched, perform actions according to the associated rule.
- If no rule matches, go to the final rule (deny all or allow all) which is specified upon policy creation.
The OneFS firewall automatically reserves 20,000 rules in the ipfw table for its custom and default policies and rules. By default, each policy can gave a maximum of 100 rules, including one default rule. This translates to an effective maximum of 99 user-defined rules per policy, because the default rule is reserved and cannot be modified. As such, a maximum of 198 policies can be applied to pools or subnets since the default-pools-policy and default-subnets-policy are reserved and cannot be deleted.
Additional firewall bounds and limits to keep in mind include:
| Name | Value | Description |
| MAX_INTERFACES | 500 | Maximum number of Layer 2 interfaces per node (including Ethernet, VLAN, LAGG interfaces). |
| MAX _SUBNETS | 100 | Maximum number of subnets within a OneFS cluster |
| MAX_POOLS | 100 | Maximum number of network pools within a OneFS cluster |
| DEFAULT_MAX_RULES | 100 | Default value of maximum rules within a firewall policy |
| MAX_RULES | 200 | Upper limit of maximum rules within a firewall policy |
| MAX_ACTIVE_RULES | 5000 | Upper limit of total active rules across the whole cluster |
| MAX_INACTIVE_POLICIES | 200 | Maximum number of policies which are not applied to any network subnet or pool. They will not be written into ipfw table. |
The firewall default global policy is ready to use out of box and, unless a custom policy has been explicitly configured, all network pools use this global policy. Custom policies can be configured by either cloning and modifying an existing policy or creating one from scratch.
| Component | Description |
| Custom policy | A user-defined container with a set of rules. A policy can be applied to multiple network pools, but a network pool can only apply one policy.
|
| Firewall rule | An ipfw-like rule which can be used to restrict remote access. Each rule has an index which is valid within the policy. Index values range from 1 to 99, with lower numbers having higher priority. Source networks are described by IP and netmask, and services can be expressed either by port number (ie. 80) or service name (ie. http,ssh,smb). The ‘*‘ wildcard can also be used to denote all services. Supported actions include ‘allow’, ‘drop’ and ‘reject’. |
| Default policy | A global policy to manage all default services, used for maintaining OneFS minimum running and management. While ‘Deny any‘ is the default action of the policy, the defined service rules have a default action to ‘allow all remote access’. All packets not matching any of the rules are automatically dropped.
Two default policies: · default-pools-policy · default-subnets-policy Note that these two default policies cannot be deleted, but individual rule modification is permitted in each. |
| Default services | The firewall’s default pre-defined services include the usual suspects, such as: DNS, FTP, HDFS, HTTP, HTTPS, ICMP, NDMP, NFS, NTP, S3, SMB, SNMP, SSH, etc. A full listing is available via the ‘isi network firewall services list’ CLI command output. |
For a given network pool, either the global policy or a custom policy is assigned and takes effect. Additionally, all configuration changes to either policy type are managed by gconfig and are persistent across cluster reboots.
In the next article in this series we’ll take a look at the configuration and management of the OneFS firewall.