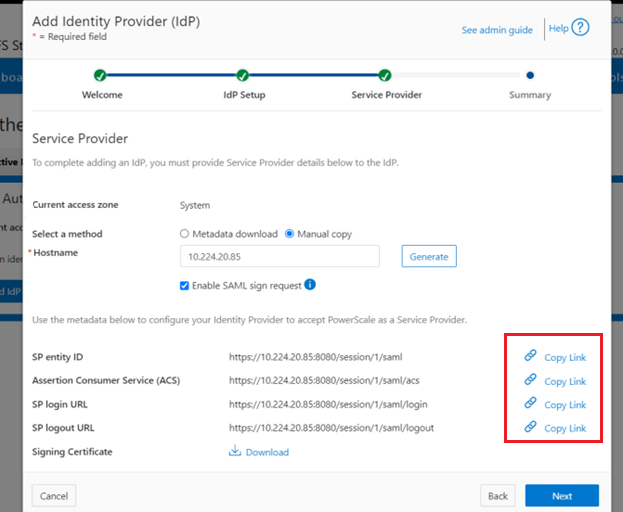
As on-the-wire encryption becomes increasingly commonplace, and often mandated via regulatory compliance security requirements, the policies applied in enterprise networks are rapidly shifting towards fully encrypting all traffic.
The OneFS SMB protocol implementation (lwio) has supported encryption for Windows and other SMB client connections to a PowerScale cluster since OneFS 8.1.1, as detailed in this article.
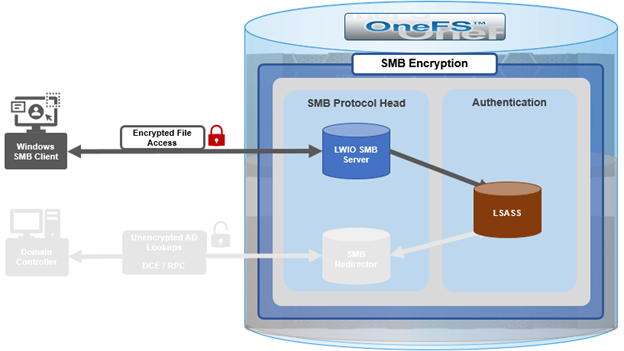
However, prior to OneFS 9.5, this did not include encrypted communications between the SMB redirector and Active Directory (AD) domain controller (DC). While Microsoft added support for SMB encryption in SMB 3.0, the redirector in OneFS 9.4 and prior releases only supported Microsoft’s earlier SMB 2.002 dialect.
When OneFS connects to Active Directory for tasks requiring remote procedure calls (RPCs), such as joining a domain, NTLM authentication, or resolving usernames and SIDs, these SMB connections are established from OneFS as the client connecting to a domain controller server.
As outlined in the Windows SMB security documentation, by default, and starting with Windows 2012 R2, domain admins can choose to encrypt access to a file share, which can include a domain controller. When encryption is enabled, only SMB3 connections are permitted.
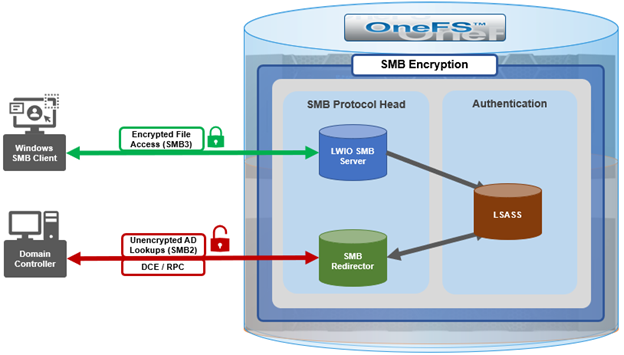
With OneFS 9.5, the OneFS SMB redirector now supports SMB3, thereby allowing the Local Security Authority Subsystem Service (LSASS) daemon to communicate with domain controllers running Windows Server 2012 R2 and later over an encrypted session.
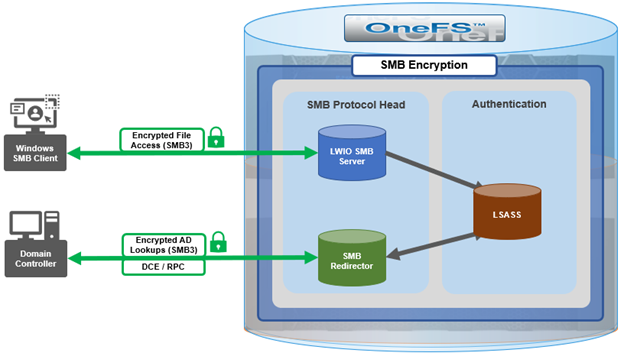
The OneFS redirector, also known as the ‘rdr driver’, is a stripped-down SMB client with minimal functionality, only supporting what is absolutely necessary.
Under the hood, OneFS SMB encryption and decryption use standard OpenSSL functions, and AES-128-CCM encryption is negotiated during SMB negotiate phase.
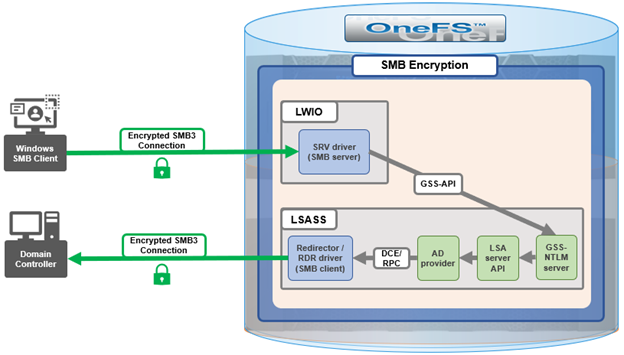
Although everything stems from the NTLM authentication requested by SMB server, the sequence of calls leads to the redirector establishing an SMB connection to the AD domain controller.
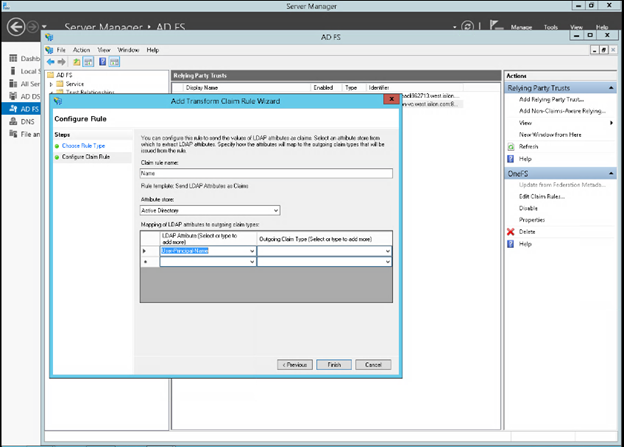
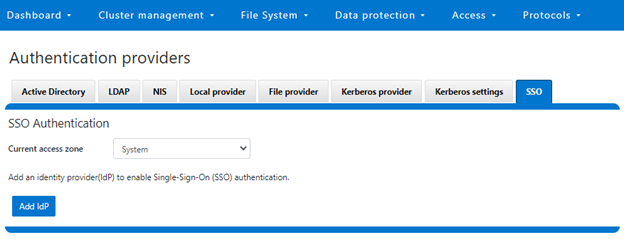
With OneFS 9.5, no configuration is required to enable SMB encryption in most situations, and there are no WebUI OR CLI configuration settings for the redirector.
With the default OneFS configuration, the redirector supports encryption if negotiated but it does not require it. Similarly, if the Active Directory domain requires encryption, the OneFS redirector will automatically enable and use encryption. However, if the OneFS redirector is explicitly configured to require encryption and the domain controller does not support encryption, the connection will fail.
The OneFS redirector encryption settings include:
| Key | Values | Description |
| Smb3EncryptionEnabled | Boolean. Default is ‘1’ == Enabled | Enable or disable SMB3 encryption for OneFS redirector. |
| Smb3EncryptionRequired | Boolean. Default is ‘0’ == Not required. | Require or not require redirector connection to be encrypted. |
| MaxSmb2DialectVersion | Default is ‘max’ == SMB 3.0.2 | Set the SMB dialect the redirector will support. Maximum is currently SMB 3.0.2. |
The above keys and values are stored in the OneFS Likewise SMB registry and can be viewed and configured with the ‘lwreqshell’ utility. For example, to view the SMB redirector encryption config settings:
# /usr/likewise/bin/lwregshell list_values "HKEY_THIS_MACHINE\Services\lwio\Parameters\Drivers\rdr" | grep -i encrypt "Smb3EncryptionEnabled" REG_DWORD 0x00000001 (1) "Smb3EncryptionRequired" REG_DWORD 0x00000000 (0)
The following syntax can be used to disable the ‘Smb3EncryptionRequired’ parameter by setting it to value ‘1’:
# /usr/likewise/bin/lwregshell set_value "[HKEY_THIS_MACHINE\Services\lwio\Parameters\Drivers\rdr]" "Smb3EncryptionRequired" "0x00000001" # /usr/likewise/bin/lwregshell list_values "HKEY_THIS_MACHINE\Services\lwio\Parameters\Drivers\rdr" | grep -i encrypt "Smb3EncryptionEnabled" REG_DWORD 0x00000001 (1) "Smb3EncryptionRequired" REG_DWORD 0x00000001 (1)
Similarly, to restore the ‘Smb3EncryptionRequired’ parameter’s default value of ‘0’ (ie. not required):
# /usr/likewise/bin/lwregshell set_value "[HKEY_THIS_MACHINE\Services\lwio\Parameters\Drivers\rdr]" "Smb3EncryptionEnabled" "0x00000001"
Note that, during the upgrade to OneFS 9.5, any nodes still running the old version will not be able to NTLM-authenticate if the DC they have affinity with requires encryption.
While redirector encryption is implemented in user space (in contrast to the SMB server, which is in the kernel), since it involves OpenSSL, the library does take advantage of hardware acceleration on the processor and utilizes AES-NI. As such, performance is only minimally impacted when the number of NTLM authentications to the AD domain is very large.
Also note that redirector encryption also only currently supports only AES-128-CCM encryption provided in the SMB 3.0.0 and 3.0.2 dialects. OneFS does not use AES-128-GCM encryption, available in the SMB 3.1.1 dialect (the latest), at this time.
When it comes to troubleshooting the redirector, the lwregshell tool can be used to verify its configuration settings. For example, to view the redirector encryption settings:
# /usr/likewise/bin/lwregshell list_values "HKEY_THIS_MACHINE\Services\lwio\Parameters\Drivers\rdr" | grep -i encrypt "Smb3EncryptionEnabled" REG_DWORD 0x00000001 (1) "Smb3EncryptionRequired" REG_DWORD 0x00000000 (0)
Similarly, to find the maximum SMB version supported by the redirector:
# /usr/likewise/bin/lwregshell list_values "HKEY_THIS_MACHINE\Services\lwio\Parameters\Drivers\rdr" | grep -i dialect "MaxSmb2DialectVersion" REG_SZ "max"
The ‘lwsm’ CLI utility with the following syntax will confirm the status of the various lsass components:
# /usr/likewise/bin/lwsm list | grep lsass lsass [service] running (lsass: 5164) netlogon [service] running (lsass: 5164) rdr [driver] running (lsass: 5164)
It can also be used to show and modify the logging level. For example:
# /usr/likewise/bin/lwsm get-log rdr <default>: syslog LOG_CIFS at WARNING # /usr/likewise/bin/lwsm set-log-level rdr - debug # /usr/likewise/bin/lwsm get-log rdr <default>: syslog LOG_CIFS at DEBUG
When finished, rdr logging can be returned to its previous log level as follows:
# /usr/likewise/bin/lwsm set-log-level rdr - warning # /usr/likewise/bin/lwsm get-log rdr <default>: syslog LOG_CIFS at WARNING
Additionally, the existing ‘lwio-tool’ utility has been modified in OneFS 9.5 to include functionality allowing simple test connections to domain controllers (no NTLM) via the new ‘rdr’ syntax:
# /usr/likewise/bin/lwio-tool rdr openpipe //<domain_controller>/NETLOGON
The ‘lwio-tool’ usage in OneFS 9.5 is as follows:
# /usr/likewise/bin/lwio-tool -h Usage: lwio-tool <command> [command-args] commands: iotest rundown rdr [openpipe|openfile] username@password://domain/path srvtest transport [query|start|stop] testfileapi [create|createnp] <path>