OneFS auditing can detect potential sources of data loss, fraud, inappropriate entitlements, access attempts that should not occur, and a range of other anomalies that are indicators of risk. This can be especially useful when the audit associates data access with specific user identities.
In the interests of data security, OneFS provides ‘chain of custody’ auditing by logging specific activity on the cluster. This includes OneFS configuration changes plus NFS, SMB, and HDFS client protocol activity, which are required for organizational IT security compliance, as mandated by regulatory bodies like HIPAA, SOX, FISMA, MPAA, etc.
OneFS auditing uses Dell’s Common Event Enabler (CEE) to provide compatibility with external audit applications. A cluster can write audit events across up to five CEE servers per node in a parallel, load-balanced configuration. This allows OneFS to deliver an end to end, enterprise grade audit solution which efficiently integrates with third party solutions like Varonis DatAdvantage.
The following diagram outlines the basic architecture of OneFS audit:
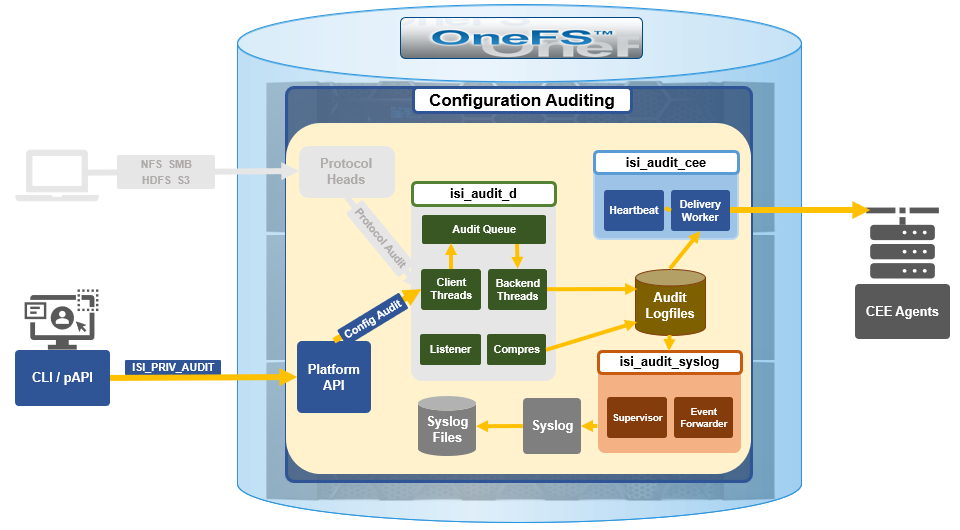
Both system configuration changes, as well as protocol activity, can be easily audited on a PowerScale cluster. However, the protocol path is greyed out above, since it is outside the focus of this article. More information on OneFS protocol auditing can be found here.
As illustrated above, the OneFS audit framework is centered around three main services.
| Service | Description |
| isi_audit_cee | Service allowing OneFS to support third-party auditing applications. The main method of accessing protocol audit data from OneFS is through a third-party auditing application. |
| isi_audit_d | Responsible for per-node audit queues and managing the data store for those queues. It provides a protocol on which clients may produce event payloads within a given context. It establishes a Unix domain socket for queue producers and handles writing and rotation of log files in /ifs/.ifsvar/audit/logs/node###/{config,protocol}/*. |
| isi_audit_syslog | Daemon providing forwarding of audit config and protocol events to syslog. |
The basic configuration auditing workflow sees a cluster config change request come in via either the OneFS CLI, WebUI or platform API. The API handler infrastructure passes this request to the isi_audit_d service, which intercepts it as a client thread and adds it to the audit queue. It is then processed and passed via a backend thread and written to the audit log files (IFS) as appropriate.
If audit syslog forwarding has been configured, IFS also passes the event to the isi_audit_syslog daemon, where a supervisor process instructs a writer thread to send it to the syslog, which in turn updates its pertinent /var/log/ logfiles.
Similarly, if Common Event Enabler (CEE) forwarding has been enabled, IFS will also pass the request to the isi_audit_cee service, where a delivery worker threads will intercept it and send the event to the CEE server pool. The isi_audit_cee heartbeat task makes CEE servers available for audit event delivery. Only after a CEE server has received a successful heartbeat will audit events be delivered to it. Every ten seconds the heartbeat task wakes up and sends each CEE server in the configuration a heartbeat. While CEE servers are available and events are in memory an attempt will be made to deliver these. Shutdown will only save audit log position if all the events are delivered to CEE since audit should not lose events. It isn’t critical that all events are delivered at shutdown since any unsaved events can be resent to CEE on the next start of isi_audit_cee since CEE handles duplicates.
Within OneFS, all audit data is organized by topic and is securely stored in the file system.
# isi audit topics list Name Max Cached Messages ----------------------------- protocol 2048 config 1024 ----------------------------- Total: 2
Auditing can detect a variety of potential sources of data loss. These include unauthorized access attempts, inappropriate entitlements, plus a bevy of other fraudulent activities that plague organizations across the gamut of industries. Enterprises are increasingly tasked required to comply with stringent regulatory mandates developed to protect against these sources of data theft and loss.
OneFS system configuration auditing is designed to track and record all configuration events that are handled by the API through the command-line interface (CLI).
# isi audit topics view config Name: config Max Cached Messages: 1024
Once enabled, system configuration auditing requires no additional configuration, and auditing events are automatically stored in the config audit topic directories. Audit access and management is governed by the ‘ISI_PRIV_AUDIT’ RBAC privilege, and OneFS provides a default ‘AuditAdmin’ role for this purpose.
Audit events are stored in a binary file under /ifs/.ifsvar/audit/logs. The logs automatically roll over to a new file after the size reaches 1 GB. The audit logs are consumable by auditing applications that support the Dell Common Event Enabler (CEE).
OneFS audit topics and settings can easily be viewed and modified. For example, to increase the configuration auditing maximum cached messages threshold to 2048 from the CLI:
# isi audit topics modify config --max-cached-messages 2048 # isi audit topics view config Name: config Max Cached Messages: 2048
Audit configuration can also be modified or viewed per access zone and/or topic.
| Operation | CLI Syntax | Method and URI |
| Get audit settings | isi audit settings view | GET <cluster-ip:port>/platform/3/audit/settings |
| Modify audit settings | isi audit settings modify … | PUT <cluster-ip:port>/platform/3/audit/settings |
| View JSON schema for this resource, including query parameters and object properties info. | GET <cluster-ip:port>/platform/3/audit/settings?describe | |
| View JSON schema for this resource, including query parameters and object properties info. | GET <cluster-ip:port>/platform/1/audit/topics?describe |
Configuration auditing can be enabled on a cluster from either the CLI or platform API. The current global audit configuration can be viewed as follows:
# isi audit settings global view Protocol Auditing Enabled: No Audited Zones: - CEE Server URIs: - Hostname: Config Auditing Enabled: No Config Syslog Enabled: No Config Syslog Servers: - Config Syslog TLS Enabled: No Config Syslog Certificate ID: Protocol Syslog Servers: - Protocol Syslog TLS Enabled: No Protocol Syslog Certificate ID: System Syslog Enabled: No System Syslog Servers: - System Syslog TLS Enabled: No System Syslog Certificate ID: Auto Purging Enabled: No Retention Period: 180 System Auditing Enabled: No
In this case, configuration auditing is disabled – its default setting. The following CLI syntax will enable (and verify) configuration auditing across the cluster:
# isi audit settings global modify --config-auditing-enabled 1 # isi audit settings global view | grep -i 'config audit' Config Auditing Enabled: Yes
In the next article, we’ll look at the config audit management, event viewing, and troubleshooting.