The Dell PowerScale Cybersecurity Suite represents a forward-thinking, integrated approach to addressing the growing challenges in cybersecurity and disaster recovery.
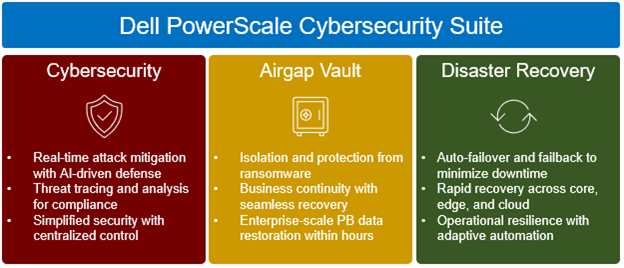
It aligns with Gartner’s definition of Cyberstorage, a category of solutions specifically designed to secure data storage systems against modern threats. These threats include ransomware, data encryption attacks, and theft, and the emphasis of Cyberstorage is on active prevention, early detection, and the ability to block attacks before they cause damage. Recovery capabilities are also tailored to the unique demands of data storage environments, making the protection of data itself a central layer of defense.
Unlike traditional solutions that often prioritize post-incident recovery – leaving organizations exposed during the critical early stages of an attack – Dell’s PowerScale Cybersecurity Suite embraces the Cyberstorage paradigm by offering a comprehensive set of capabilities that proactively defend data and ensure operational resilience. These include:
| Capability | Details |
| Active Defense at the Data Layer | The suite integrates AI-driven tools to detect and respond to threats in real-time, analyzing user behavior and unauthorized data access attempts. Bidirectional threat intelligence integrates seamlessly into SIEM, SOAR, and XDR platforms for coordinated protection at every layer. |
| Automated Threat Prevention | Includes features like automated snapshots, operational air-gapped vaults, and immediate user lockouts to stop attacks before damage spreads. Attack simulation tools also ensure that the defenses are always optimized for emerging threats. |
| NIST Framework Alignment | Adheres to the National Institute of Standards and Technology (NIST) cybersecurity framework, providing a structured approach to identifying, protecting, detecting, responding to, and recovering from threats. This comprehensive protection eliminates vulnerabilities overlooked by traditional backup and security tools, enabling organizations to stay ahead of today’s evolving cyber risks while ensuring business continuity. |
| Rapid Recovery and Resilience | With secure backups and precision recovery, organizations can rapidly restore specific files or entire datasets without losing unaffected data. Recovery is accelerated by integrated workflows that minimize downtime. |
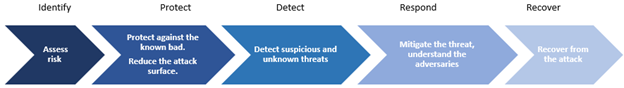
By embedding detection, protection, and response directly into the data layer, the Dell PowerScale Cybersecurity Suite adopts a proactive and preventive approach to safeguarding enterprise environments:
| Approach | Details |
| Identification & Detection | Detecting potential incursions in real time using AI-driven behavioral analytics. |
| Protection | Protecting data at its source with advanced security measures and automated threat monitoring. |
| Response | Responding decisively with automated remediation to minimize damage and accelerate recovery, ensuring seamless continuity. |
| Recovery | Providing recovery tools and forensic data and recovery tools to quickly restore clean data in the event of a breach, minimizing business disruption. |
It begins with identification and detection, where data is protected at its source through advanced security measures and continuous automated threat monitoring. Protection is achieved by identifying potential incursions in real time using AI-driven behavioral analytics, allowing organizations to act before threats escalate. When a threat is detected, the suite responds with automated remediation processes that minimize damage and accelerate recovery, ensuring uninterrupted operations.
This integrated approach enables Dell to address the full lifecycle of security and recovery within the PowerScale platform, delivering exceptional resilience across IT environments.
Released globally on August 28, 2025, the Dell PowerScale Cybersecurity Suite is available in three customizable bundles tailored to meet diverse operational and regulatory needs.
| Bundle | Details |
| Cybersecurity Bundle | Leverages AI-driven threat detection, Zero Trust architecture, and automated risk mitigation to fortify security. |
| Airgap Vault Bundle | Extends the capabilities of the Cybersecurity Bundle by adding isolated, secure backups for robust ransomware protection. This bundle requires the Cybersecurity Bundle and the Disaster Recovery Bundle.. |
| Disaster Recovery Bundle | Prioritizes rapid recovery with near-zero Recovery Point Objectives (RPO), Recovery Time Objectives (RTO), and seamless failover capabilities. |
The Cybersecurity Bundle leverages AI-driven threat detection, Zero Trust architecture, and automated risk mitigation to strengthen data protection. The Airgap Vault Bundle builds on this by adding isolated, secure backups for enhanced ransomware defense, and requires both the Cybersecurity and Disaster Recovery bundles for full deployment. The Disaster Recovery Bundle focuses on rapid recovery, offering rapid Recovery Point Objectives (RPO) and Recovery Time Objectives (RTO), along with seamless failover capabilities to ensure business continuity.
Customers can choose specific bundles based on their requirements, with the only prerequisite being that the Airgap Vault bundle must be deployed alongside both the Cybersecurity and Disaster Recovery bundles to ensure full functionality and integration.
Built upon the venerable PowerScale platform, the suite is engineered to protect unstructured data and maintain operational availability in today’s increasingly complex threat landscape. As such, it offers a comprehensive set of tools, techniques, and architectural flexibility to deliver multilayered security and responsive recovery.
This enables organizations to design robust solutions that align with their specific security priorities—from advanced threat detection to seamless disaster recovery.
Among its key benefits, the suite includes automated threat response capabilities that swiftly mitigate risks such as malicious data encryption and exfiltration.
| Feature | Details |
| Automated threat response | The suite features automated responses to cybersecurity threats, such as data encryption, and the prevention of data exfiltration, helping mitigate risks swiftly and effectively. |
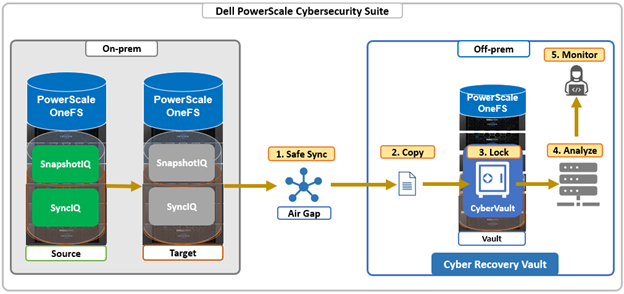
| Secure Operational Airgap Vault | Data is protected within an isolated operational airgap vault, and will only be transferred to the operational airgap vault if the production storage environment is not under attack, ensuring critical assets remain secure and inaccessible to unauthorized actors. |
| Ecosystems Integration | Seamlessly integrates with leading endpoint protection and incident response software, automating and simplifying operations during a cyberattack to ensure a coordinated and efficient response. |
| DoD-Certified Hardware Integration | Designed to enhance PowerScale’s DoD APL certified hardware, meeting rigorous cybersecurity standards, and providing customers with a trusted platform on which to build their defenses. The suite’s advanced capabilities, robust protection, and proven hardware deliver a comprehensive cyber and DR solution tailored to meet today’s complex security challenges. |
It also features a secure operational airgap vault, which ensures that data is only transferred when the production environment is verified to be safe, keeping critical assets isolated and protected from unauthorized access. Integration with leading endpoint protection and incident response platforms allows for coordinated and efficient responses during cyberattacks, streamlining operations and reducing complexity.
The suite is also designed to complement PowerScale’s DoD APL-certified hardware, meeting stringent cybersecurity standards and providing a trusted foundation for enterprise defense strategies. Its advanced capabilities, combined with proven hardware, deliver a comprehensive cybersecurity and disaster recovery solution tailored to modern security challenges.
The Dell PowerScale Cybersecurity Suite is engineered to support petabyte-scale environments containing billions of files distributed across multiple PowerScale clusters. There is no hard-coded limit on the volume of data it can manage. However, actual throughput and failover times are influenced by factors such as SyncIQ bandwidth, the degree of policy parallelism, and the overall readiness of the environment. To help forecast recovery timelines, the suite includes an Estimated Failover Time engine that uses real metrics to generate policy-specific projections.
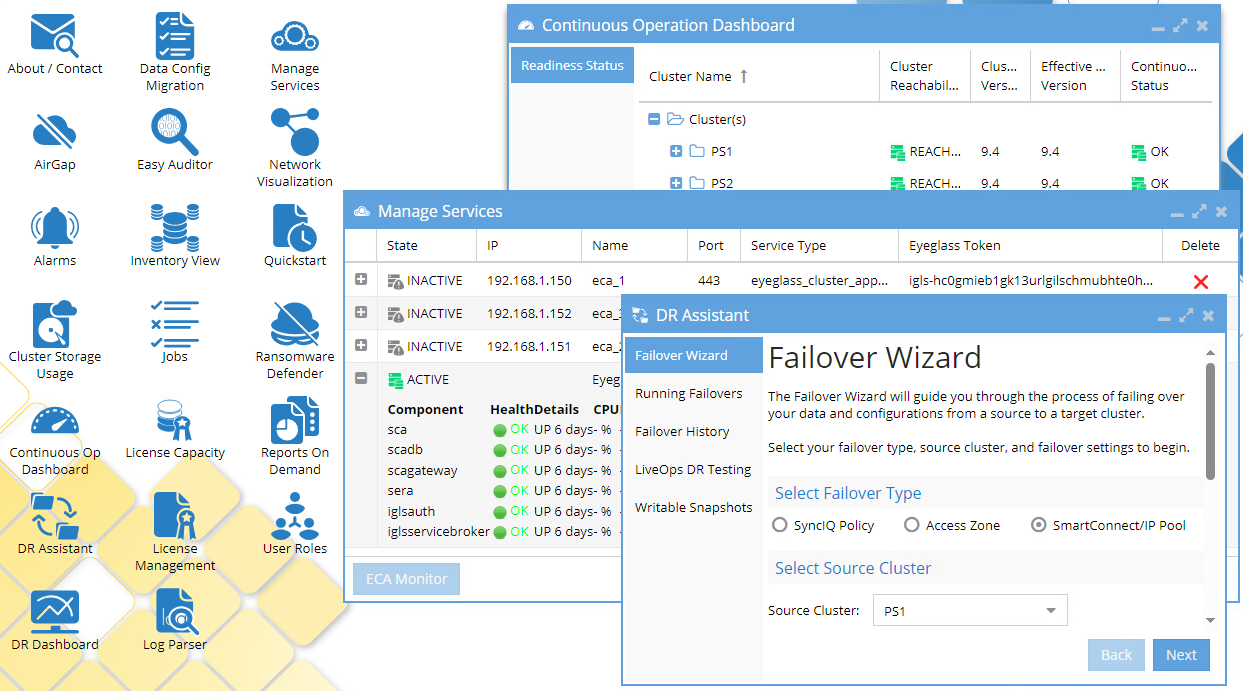
Superna software, which underpins the suite, interacts with PowerScale systems via REST APIs. These APIs provide access to inventory data, facilitate the orchestration of snapshot creation and deletion, and enable user lockout and restoration of access to shared resources. Specifically, the suite utilizes the file system API and the system configuration API to perform these operations. Meanwhile, configuration and management can be performed via the comprehensive, intuitive WebUI:
The performance impact of running the Data Security Edition—which includes the Cybersecurity Bundle with Ransomware Defender and Easy Auditor—is primarily tied to the frequency and volume of API calls made to PowerScale. These calls can be managed and tuned by administrators and support teams during deployment and system configuration. One known scenario that may affect cluster performance occurs when user permissions are broadly configured to allow all users access to all shares. In such cases, default settings combined with enabled snapshots can lead to excessive API endpoint activity, as the system attempts to create and delete snapshots across all shares. To mitigate this, Dell recommends disabling default snapshots during deployment and instead configuring snapshots only for critical data paths. Outside of this specific configuration, Dell has not identified any significant performance impacts under normal operating conditions.
The Dell-branded software is built on the same codebase as the standard Superna 2.x release, with branding determined by licensing. This branding helps ensure consistency, simplify user interactions, and reinforce the alignment between the suite and Dell Technologies’ broader product portfolio.
With regard to release cadence, there is typically a 60-day lead time between Superna releasing a new version and Dell launching its branded equivalent, allowing for additional QA, regression, and longevity testing.
With the Cybersecurity suite, Dell Technologies will directly manage implementation services and provide first-call support. This approach ensures a seamless and customer-focused experience, with faster response times and streamlined service delivery. It also guarantees that customers receive consistent and integrated support throughout their deployment and operational lifecycle.
It is important to note that Dell-branded and Superna-branded software cannot be mixed within the same PowerScale cluster. Currently, the Dell PowerScale Cybersecurity Suite is intended exclusively for new deployments and is not compatible with existing Superna-branded environments. Migration from Superna to Dell-branded software is not supported at this time, unless an entire Superna Eyeglass solution is being renewed. However, Dell is actively working to expand migration options in future releases.