As we saw in the previous article in this series, OneFS Multi-party Authorization (MPA) requires that one or more additional trusted parties sign off on requested changes for certain privileged actions within a PowerScale cluster.
A prerequisite to enabling MPA in OneFS 9.12 is the requirement for two users with the approval privilege, both registered as internal approvers. Once MPA has been activated on a cluster, any of the predefined ‘privileged actions’ will require explicit approval. In order for a privileged action, such as secure snapshot deletion, to complete, one of the registered MPA approvers must bless the PAA request. Finally, assuming approval was granted, the privileged action can be executed.
The MPA privileged action approval workflow can be summarized in the following request state diagram:
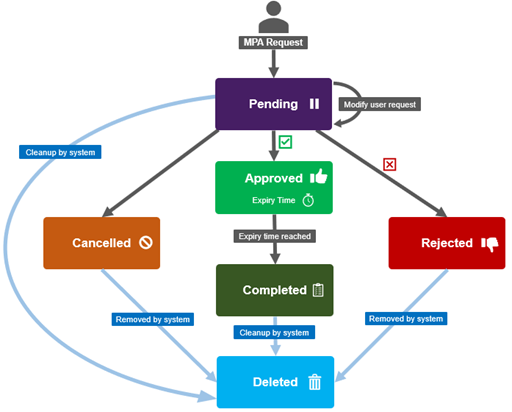
Under the hood, MPA request lifecycle configuration data is stored in the form of key-value pairs, and the MPA Approvers registration status, PAA requests, and request approval details are kept in a shared SQLite database.
Note that MPA approver users can only reside in the System multi-tenant access zone and require the new ISI_PRIV_MPA_APPROVAL and ISI_PRIV_MPA_REQUEST privileges at a minimum.
MPA includes privileged actions, which extend across the S3 protocol, supporting immutable bucket retention and logging, cluster hardening, and the main one which is the new secure snapshots functionality.
As such, the full complement of these privileged actions in OneFS 9.12 is as follows:
| Service /
Component |
Action | Description |
| MPA | register_approval_admin | Registering approval admin becomes a privilege action once MPA is enabled. |
| MPA | upload_trust_anchor | Upload a trust anchor certificate after MPA is enabled. |
| Privileged CLI | cli_mpa_check | MPA check to execute specific CLI command. Eg. once root lockdown mode is enabled, elevate to root will use this. |
| Hardening | apply_hardening | Applying a Hardening Profile, such as root-lockdown, STIG. |
| Hardening | disable_hardening | Disabling a Hardening Profile, such as root-lockdown, STIG. |
| S3 | reduce_immutable_bucket_retention | Reduce bucket retention for an immutable bucket. |
| S3 | modify_server_access_logging_config | Change a bucket’s access logging configuration. |
| Platform | reduce_immutable_bucket_retention | Reduce bucket retention for an immutable bucket. |
| Platform | modify_server_access_logging_config | Changing a bucket’s access logging configuration. |
| Snapshot | delete_snapshot | Delete a snapshot. |
| modify_snapshot | Modify a snapshot. | |
| delete_snapshot_schedule | Delete a snapshot’s schedule. | |
| modify_snapshot_schedule | Modify a snapshot’s schedule. |
A number of new RBAC privileges are introduced in 9.12 to support MPA, including MPA request, MPA approval, which allows an approver to bless or reject a privileged action request, plus MPA upload, global and multi-tenant access zone settings:
| MPA Privilege | Description | Permission |
| ISI_PRIV_MPA_APPROVAL | Privilege for MPA approver to approve or reject MPA request. | Write |
| ISI_PRIV_MPA_REQUEST | Privilege required for MPA request APIs. | Write/Read |
| ISI_PRIV_MPA_SETTINGS_GLOBAL | Privilege required to enable MPA. | Write |
| ISI_PRIV_MPA_SETTINGS_ZONE | Privilege required to read MPA metadata/ MPA request-lifecycle settings. | Read |
| ISI_PRIV_SIGNED_APPROVAL_UPLOAD | Upload signed approval for Multi-Party Authorization Requests. (Applicable for 3rd party MPA only) | Write |
There’s also the new ‘Approval Admin’ default role, and a number of other roles that see the addition of MPA privileges, including SecurityAdmin, SystemAdmin, zone admin, and basic user, etc.
The ApprovalAdmin role is automatically assigned all the required privileges for MPA approval and configuration. For example:
# isi auth roles list | grep -i appr ApprovalAdmin # isi auth roles view ApprovalAdmin Name: ApprovalAdmin Description: Allows MPA request approval. Members: root admin Privileges ID: ISI_PRIV_LOGIN_PAPI Permission: + ID: ISI_PRIV_MPA_APPROVAL Permission: w ID: ISI_PRIV_MPA_REQUEST Permission: w ID: ISI_PRIV_MPA_SETTINGS_GLOBAL Permission: r ID: ISI_PRIV_MPA_SETTINGS_ZONE Permission: r
The minimum MPA privileges required are ISI_PRIV_MPA_APPROVAL and ISI_PRIV_MPA_REQUEST.
Here are the system multi-tenant access zone roles that see the addition of MPA privileges in OneFS 9.12:
| System Zone Roles | Privilege | Permission |
| ApprovalAdmin | ISI_PRIV_MPA_APPROVAL | Write |
| ISI_PRIV_MPA_REQUEST | Write | |
| ISI_PRIV_MPA_SETTINGS_GLOBAL | Read | |
| ISI_PRIV_MPA_SETTINGS_ZONE | Read | |
| BasicUserRole | ISI_PRIV_MPA_REQUEST | Write |
| ISI_PRIV_MPA_SETTINGS_ZONE | Read | |
| SecurityAdmin | ISI_PRIV_MPA_REQUEST | Write |
| ISI_PRIV_MPA_SETTINGS_GLOBAL | Write | |
| ISI_PRIV_MPA_SETTINGS_ZONE | Read | |
| SystemAdmin | ISI_PRIV_MPA_REQUEST | Write |
| ISI_PRIV_MPA_SETTINGS_GLOBAL | Read | |
| ISI_PRIV_MPA_SETTINGS_ZONE | Read |
Similarly, the OneFS 9.12 MPA privileges for non-system multi-tenant access zone roles:
| Non-System Zone Roles | Privilege | Permission |
| BasicUserRole | ISI_PRIV_MPA_REQUEST | Write |
| ISI_PRIV_MPA_SETTINGS_ZONE | Read | |
| ZoneAdmin | ISI_PRIV_MPA_REQUEST | Write |
| ISI_PRIV_MPA_SETTINGS_ZONE | Read | |
| ZoneSecurityAdmin | ISI_PRIV_MPA_REQUEST | Write |
| ISI_PRIV_MPA_SETTINGS_ZONE | Read |
MPA approvers can use any of a cluster’s authentication providers, such as file, local, Active Directory or LDAP, and can they grant or reject any MPA request from any multi-tenant access zone. However, an approver cannot approve their own request, regardless of whether it’s created by them or created for them.
The CLI commands and platform API endpoints for registration, query, and approval are as follows:
| MPA Action | CLI Command | Platform API Endpoint |
| Initiate (re)registration | isi mpa initiate-registration (–force) | POST /mpa/initiate-registration (?force) |
| Complete registration | isi mpa complete-registration –totp_code xxxxxx | PUT /mpa/complete-registration -d ‘{“totp_code“ : xxxxxx}’ |
| List all approvers | isi mpa approver list | GET /mpa/approvers |
| Query an approver | isi mpa approver view <ID> | GET /mpa/approvers/<ID> |
| Approve a request | isi mpa requests approve <id> –totp xxxxxx –approved true | POST /mpa/approval/<MPA-req-id> |
Note that the approver user can easily re-register at any time, say if their TOTP is lost, or for another security concern.
An approval request can be in one of five states: Approved, Cancelled, Completed, Pending, or Rejected.
These states, and their various expiry times, can be viewed with the following CLI command syntax:
# isi mpa settings request-lifecycle list Approved Description: expire in configured days for privilege action execution. Expire_time: 7d Cancelled Description: remove from system in configured days. Expire_time: 7d Completed Description: remove from system in configured days. Expire_time: 30d Pending Description: expire in configured days can be updated by user or approver. Expire_time: 7d Rejected Description: remove from system in configured days. Expire_time: 30d
The next article in this series will focus on the specific configuration, enablement, and approval procedures for MPA.