Among the slew of security enhancements introduced in OneFS 9.5 is the ability to mandate a more stringent password policy. This is required in order to comply with security requirements such as the US military STIG, which stipulates:
| Requirement | Description |
| Length | An OS or network device must enforce a minimum 15-character password length. |
| Percentage | An OS must require the change of at least 50% of the total number of characters when passwords are changed. |
| Position | A network device must require that when a password is changed, the characters are changed in at least eight of the positions within the password. |
| Temporary password | The OS must allow the use of a temporary password for system logons with an immediate change to a permanent password. |
The OneFS password security architecture can be summarized as follows:
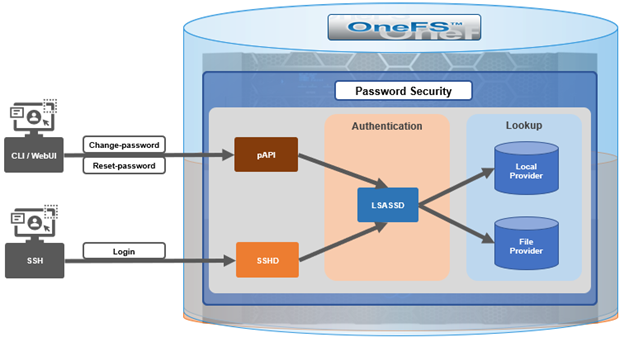
Within the OneFS security subsystem, authentication is handled in OneFS by LSASSD, the daemon used to service authentication requests for lwiod.
| Component | Description |
| LSASSD | The local security authority subsystem service (LSASS) handles authentication and identity management as users connect to the cluster. |
| File provider | The file provider includes users from /etc/password and groups from /etc/groups. |
| Local provider | The local provider includes local cluster accounts like ‘anonymous’, ‘guest’, etc. |
| SSHD | OpenSSH Daemon which provides secure encrypted communications between a client and a cluster node over an insecure network. |
| pAPI | The OneFS Platform API (PAPI), which provides programmatic interfaces to OneFS configuration and management via a RESTful HTTPS service. |
In OneFS AIMA, there are several different kinds of backend providers: Local provider, file provider, AD provider, NIS provider, etc. Each provider is responsible for the management of users and groups inside the provider. For OneFS password policy enforcement, the Local and File providers are the focus.
The local provider is based on an SamDB style file stored with prefix path of “/ifs/.ifsvar”, and its provider settings can be viewed by the following CLI syntax:
# isi auth local view System
On the other hand, the file provider is based on the FreeBSD spwd.db file, and its configuration can be viewed by the following CLI command:
# isi auth file view System
Each provider stores and manage its own users. For the local provider, ` isi auth users create’ CLI command will create a user inside the provider by default. However, for the file provider, there is no corresponding command. Instead, the `pw` CLI command can be used to create a new file provider user.
After the user is created, the `isi auth users modify <USER>` CLI command can be used to change the attributes of the user for both the file and local providers. However, not all attributes are supported for both providers. For example, the file provider does not support password expiry.
The fundamental password policy CLI changes introduced in OneFS 9.5 are as follows:
| Operation | OneFS 9.5 Change | Details |
| change-password | Modified | Needed to provide old password for changing so that we can calculate how many chars/percent changed |
| reset-password | Added | Generates a temp password that meets current password policy for user to login |
| set-password | Deprecated | Doesn’t need to provide old password |
A user’s password can now be set, changed, and reset by either ‘root’ or ‘admin’. This is supported by the new ‘isi auth users change-password’ or ‘isi auth users reset-password’ CLI command syntax. The latter, for example, returns a temporary password and requires the user to change it on next login. After logging in with the temporary (albeit secure) password, OneFS immediately forces the user to change it:
# whoami admin # isi auth users reset-password user1 4$_x\d\Q6V9E:sH # ssh user1@localhost (user1@localhost) Password: (user1@localhost) Your password has expired. You are required to immediately change your password. Changing password for user1 New password: (user1@localhost) Re-enter password: Last login: Wed May 17 08:02:47 from 127.0.0.1 PowerScale OneFS 9.5.0.0 # whoami user1
Also in OneFS 9.5 and later, the CLI ‘isi auth local view system’ command sees the addition of four new fields:
- Password Chars Changed
- Password Percent Changed
- Password Hash Type
- Max Inactivity Days
For example:
# isi auth local view system Name: System Status: active Authentication: Yes Create Home Directory: Yes Home Directory Template: /ifs/home/%U Lockout Duration: Now Lockout Threshold: 0 Lockout Window: Now Login Shell: /bin/zsh Machine Name: Min Password Age: Now Max Password Age: 4W Min Password Length: 0 Password Prompt Time: 2W Password Complexity: - Password History Length: 0 Password Chars Changed: 0 Password Percent Changed: 0 Password Hash Type: NTHash Max Inactivity Days: 0
The following CLI command syntax configures OneFS to require a minimum password length of 15 characters, a 50% or greater change, and 8 or more characters to be altered for a successful password reset:
# isi auth local modify system --min-password-length 15 --password-chars-changed 8 --password-percent-changed 50
Next, a command is issued to create a new user, ‘user2’, with a 10 character password:
# isi auth users create user2 --password 0123456789 Failed to add user user1: The specified password does not meet the configured password complexity or history requirements
This attempt fails because the password does not meet the configured password criteria (15 chars, 50% change, 8 chars to be altered).
Instead, the password for the new account, ‘user2’, is set to an appropriate value: ie ‘0123456789abcdef’. Also, the ‘–prompt-password-change’ flag is included to force the user to change their password on next login.
# isi auth users create user2 --password 0123456789abcdef –prompt-password-change 1
On logging in to the ‘user2’ account, OneFS immediately prompts for a new password. In the example below, the following non-compliant password (‘012345678zyxw’) is entered.
- 0123456789abcdef -> 012345678zyxw = Failure
This returns an unsuccessful change attempt failure, since it does not meet the 15 character minimum:
# su user2 New password: Re-enter password: The specified password does not meet the configured password complexity requirements. Your password must meet the following requirements: * Must contain at least 15 characters. * Must change at least 8 characters. * Must change at least 50% of characters. New password:
Instead, a compliant password and successful change could be:
- 0123456789abcdef -> 0123456zyxwvuts = Success
The following command can also be used to change the password for a user. For example, to update user2’s password:
# isi auth users change-password user2 Current password (hit enter if none): New password: Confirm new password:
If a non-compliant password is entered, the following error is returned:
Password change failed: The specified password does not meet the configured password complexity or history requirements
When employed, OneFS hardening automatically enforces security-based configurations. The hardening engine is profile-based, and its STIG security profile is predicated on security mandates specified in the US Department of Defense (DoD) Security Requirements Guides (SRGs) and Security Technical Implementation Guides (STIGs).
On applying the STIG hardening security profile to a cluster (‘isi hardening apply –profile=STIG’), the password policy settings are automatically reconfigured to the following values:
| Field | Normal Value | STIG Hardened |
| Lockout Duration | Now | Now |
| Lockout Threshold | 0 | 3 |
| Lockout Window | Now | 15m |
| Min Password Age | Now | 1D |
| Max Password Age | 4W | 8W4D |
| Min Password Length | 0 | 15 |
| Password Prompt Time | 2W | 2W |
| Password Complexity | – | lowercase, numeric, repeat, symbol, uppercase |
| Password History Length | 0 | 5 |
| Password Chars Changed | 0 | 8 |
| Password Percent Changed | 0 | 50 |
| Password Hash Type | NTHash | SHA512 |
| Max Inactivity Days | 0 | 35 |
For example:
# uname -or Isilon OneFS 9.5.0.0 # isi hardening list Name Description Status --------------------------------------------------- STIG Enable all STIG security settings Applied --------------------------------------------------- Total: 1 # isi auth local view system Name: System Status: active Authentication: Yes Create Home Directory: Yes Home Directory Template: /ifs/home/%U Lockout Duration: Now Lockout Threshold: 3 Lockout Window: 15m Login Shell: /bin/zsh Machine Name: Min Password Age: 1D Max Password Age: 8W4D Min Password Length: 15 Password Prompt Time: 2W Password Complexity: lowercase, numeric, repeat, symbol, uppercase Password History Length: 5 Password Chars Changed: 8 Password Percent Changed: 50 Password Hash Type: SHA512 Max Inactivity Days: 35
Note that the ‘Password Hash Type’ is changed from the default ‘NTHash’ to the more secure ‘SHA512’ encoding, in addition to setting the various password criteria.
The OneFS 9.5 WebUI also sees several additions and alterations to the Password Policy page. These include:
| Operation | OneFS 9.5 Change | Details |
| Policy page | Added | New Password policy page under Access -> Membership and Roles |
| reset-password | Added | Generate a random password that meets current password policy for user to login |
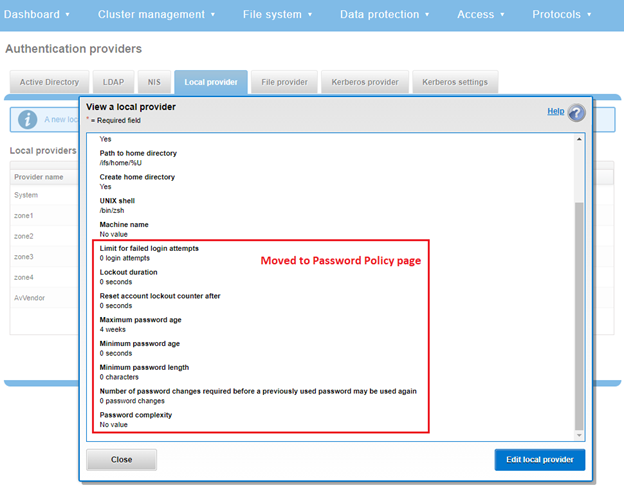
The most obvious change is the transfer of the policy configuration elements from the local provider page to a new dedicated Password Policy page.
Here’s the OneFS 9.4 ‘View a local provider’ page, under Access > Authentication providers > Local providers > System:
The above is replaced and augmented in the OneFS 9.5 WebUI with the following page, located under Access > Membership and Roles > Password Policy:
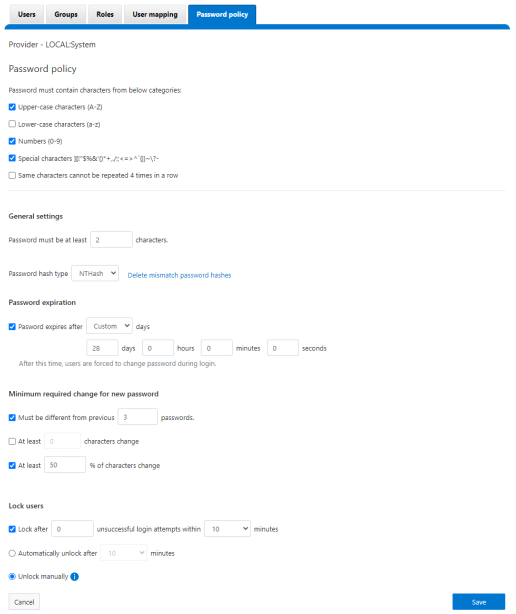
New password policy configuration options are included to require upper-case, lower-case, numeric, or special characters and limit the number of contiguous repeats of a character, etc.
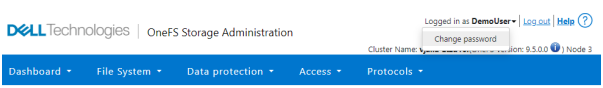
When it comes to changing a password, only a permitted user can make their change. This can be performed from a couple of locations in the WebUI. First, the user options on the task bar at the top of each screen now provides a ‘Change password’ option:
A pop-up warning message will also be displayed by the WebUI, informing when password expiration is imminent. This warning provides a ‘Change Password’ link:
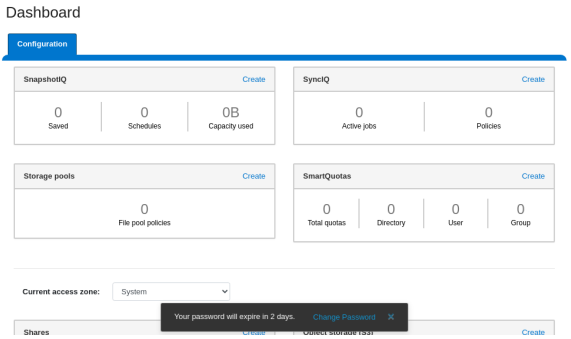
Clicking on the above link displays the following page:
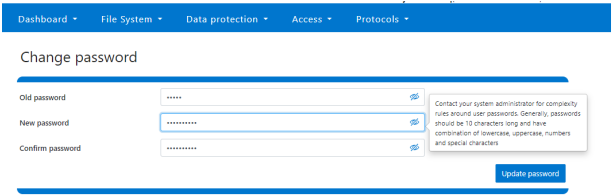
A new password complexity tool-tip message is also displayed, informing the user of safe password selection.
Note that re-login is required after a password change.
On the ‘Users’ page under Access > Membership and roles > Users, the ‘Action’ drop-down list on the ‘Users’ page now also contains a ‘Reset Password’ option:
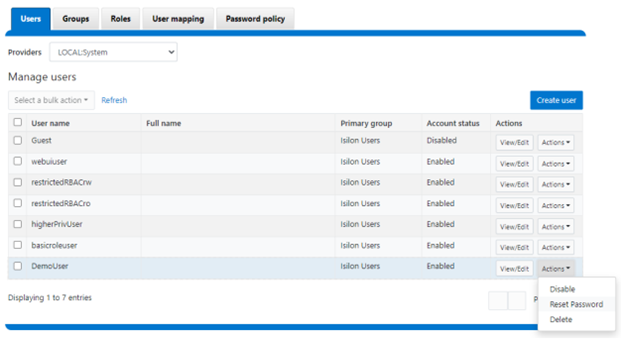
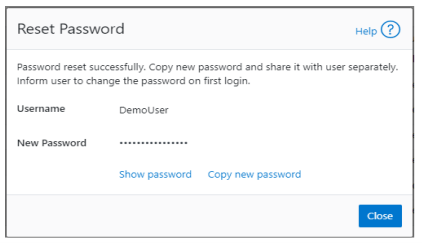
The successful reset confirmation pop-up offers both a ‘show’ and ‘copy’ option, while informing the cluster administrator to share the new password with the user, and for them to change their password during their next login:
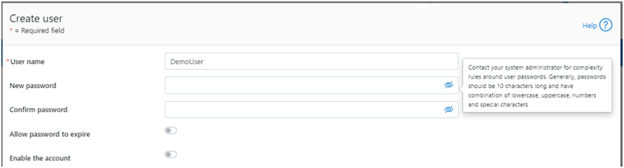
The ‘Create user’ page now provides an additional field that requires password confirmation. Additionally, the password complexity tool-tip message is also displayed:
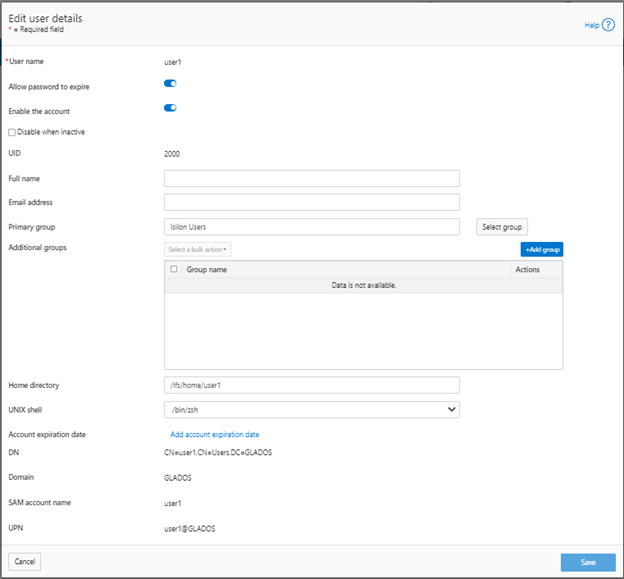
The redesigned ‘Edit user details’ page no longer provides a field to edit the password directly:
Instead, the ‘Action’ drop-down list on the ‘Users’ page now contains a ‘Reset Password’ option.